I will cut right to the chase …
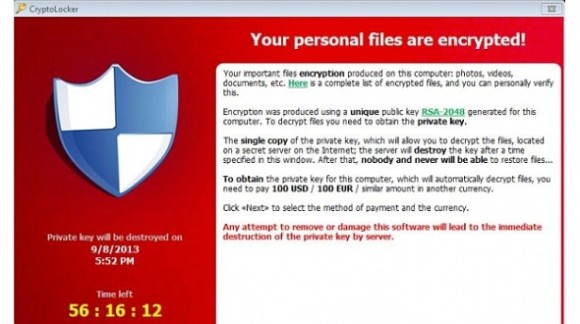
If you get the following pop up on your computer, then its probably too late. I have had 3 seperate client offices affected by this virus. The first time I paid the ransom to decrypt my files. The 2nd and 3rd time I was prepared and had backups running with rsnapshot so I was able to go back several hours to before the infection encrypted my whole server. The user who initially had the infection lost all files on the desktop and my documents since those are not backed up.
Here are some useful links on the subject
Bleeping Computer has a lot of good info: <<<<LINK>>>>
Blocking executables in %AppData% (this is where the virus runs from): <<<<LINK>>>>
I used secpol.msc on a windows XP workstation to determine what needed to be blocked. I then went into the registry and exported the following keys so that I could use a login script to apply the keys to other workstations on the network.
####Reg file contents (import into registry windows XP #####
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers\Paths]
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers\Paths\{58dca1de-6e21-4b21-8010-0481e042ef55}]
“LastModified”=hex(b):e6,37,e8,fb,4c,c4,ce,01
“Description”=”dont allow executables from AppData”
“SaferFlags”=dword:00000000
“ItemData”=hex(2):25,00,41,00,70,00,70,00,44,00,61,00,74,00,61,00,25,00,5c,00,\
2a,00,2e,00,65,00,78,00,65,00,00,00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers\Paths\{dd6f32b9-d45e-4f13-bda8-dc4276b0c763}]
“LastModified”=hex(b):86,17,44,f8,4c,c4,ce,01
“Description”=”dont allow executable from subpath in AppData”
“SaferFlags”=dword:00000000
“ItemData”=hex(2):25,00,41,00,70,00,70,00,44,00,61,00,74,00,61,00,25,00,5c,00,\
2a,00,5c,00,2a,00,2e,00,65,00,78,00,65,00,00,00